[ad_1]

A newly found Linux malware dubbed ‘DISGOMOJI’ makes use of the novel method of using emojis to execute instructions on contaminated units in assaults on authorities companies in India.
The malware was found by cybersecurity agency Volexity, which believes it’s linked to a Pakistan-based risk actor referred to as ‘UTA0137.’
“In 2024, Volexity recognized a cyber-espionage marketing campaign undertaken by a suspected Pakistan-based risk actor that Volexity at the moment tracks below the alias UTA0137,” explains Volexity.
“Volexity assesses with excessive confidence that UTA0137 has espionage-related targets and a remit to focus on authorities entities in India. Primarily based on Volexity’s evaluation, UTA0137’s campaigns seem to have been profitable,” continued the researchers.
The malware is just like many different backdoors/botnets utilized in completely different assaults, permitting risk actors to execute instructions, take screenshots, steal recordsdata, deploy further payloads, and seek for recordsdata.
Nevertheless, its use of Discord and emojis as a command and management (C2) platform makes the malware stand out from others and will enable it to bypass safety software program that appears for text-based instructions.
Discord and emojis as a C2
Based on Volexity, the malware was found after the researchers noticed a UPX-packed ELF executable in a ZIP archive, probably distributed by means of phishing emails. Volexity believes that the malware targets a customized Linux distribution named BOSS that Indian authorities companies use as their desktop.
When executed, the malware will obtain and show a PDF lure that could be a beneficiary type from India’s Defence Service Officer Provident Fund in case of an officer’s loss of life.
Nevertheless, further payloads will likely be downloaded within the background, together with the DISGOMOJI malware and a shell script named ‘uevent_seqnum.sh’ that’s used to seek for USB drives and steal information from them.
When DISGOMOJI is launched, the malware will exfiltrate system data from the machine, together with IP deal with, username, hostname, working system, and the present working listing, which is distributed again to the attackers.
To regulate the malware, the risk actors make the most of the open-source command and management undertaking discord-c2, which makes use of Discord and emojis to speak with contaminated units and execute instructions.
The malware will connect with an attacker-controlled Discord server and watch for the risk actors to kind emojis into the channel.
“DISGOMOJI listens for brand spanking new messages within the command channel on the Discord server. C2 communication takes place utilizing an emoji-based protocol the place the attacker sends instructions to the malware by sending emojis to the command channel, with further parameters following the emoji the place relevant. Whereas DISGOMOJI is processing a command, it reacts with a “Clock” emoji within the command message to let the attacker know the command is being processed. As soon as the command is totally processed, the “Clock” emoji response is eliminated and DISGOMOJI provides a “Examine Mark Button” emoji as a response to the command message to substantiate the command was executed.”
❖ Volexity
9 emojis are used to characterize instructions to execute on an contaminated gadget, that are listed under.
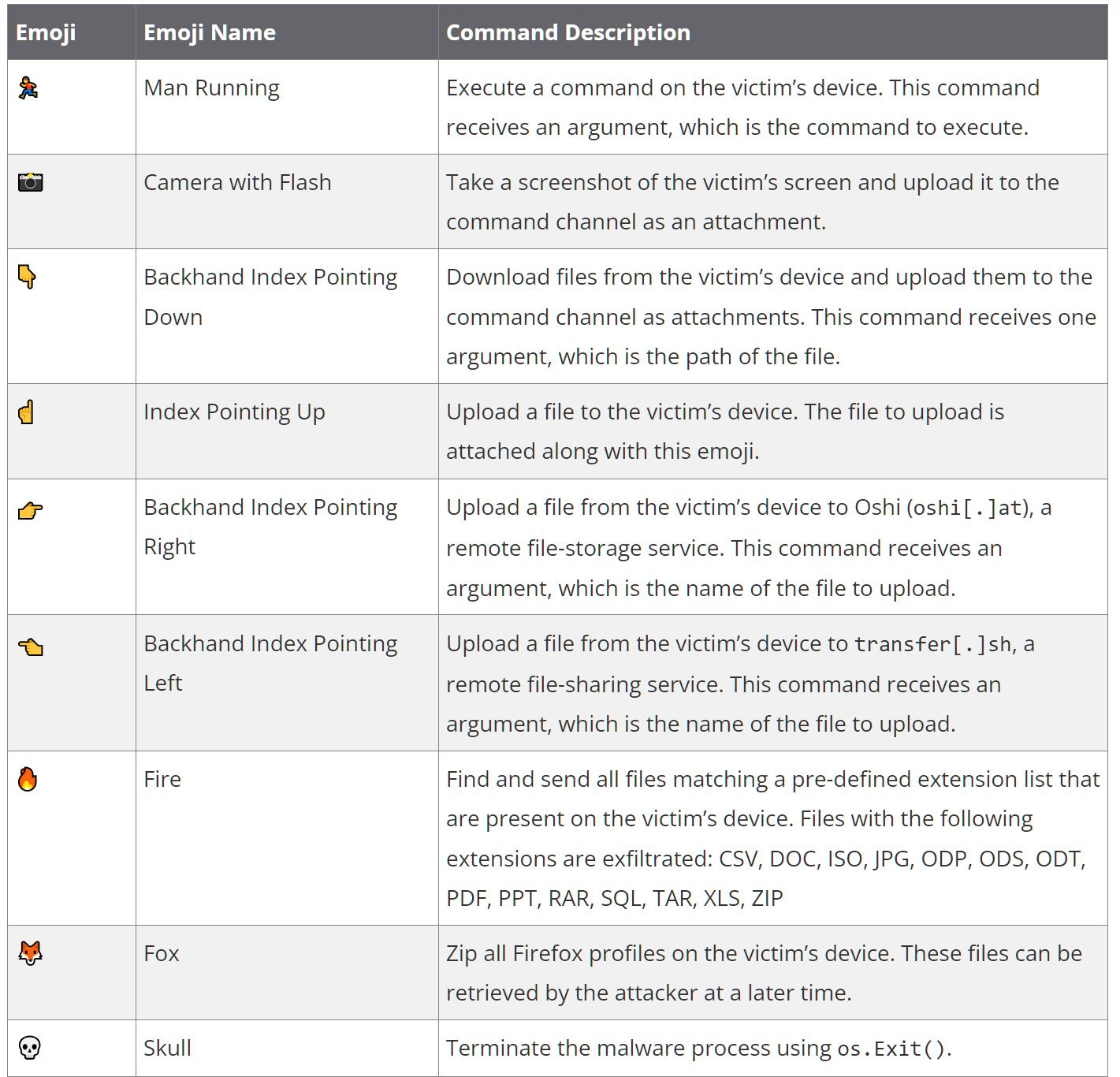
The malware maintains persistence on the Linux gadget through the use of the @reboot cron command to execute the malware on boot.
Volexity says they found further variations that utilized different persistence mechanisms for DISGOMOJI and the USB information theft script, together with XDG autostart entries.
As soon as a tool is breached, the risk actors make the most of their entry to unfold laterally, steal information, and try and steal further credentials from focused customers.
Whereas emojis could look like a “cute” novelty to the malware, they may enable it to bypass detection by safety software program that generally appears for string-based malware instructions, making this an attention-grabbing method.
[ad_2]
Leave a Reply